Why the SAFE Network Matters
Articles ·The Internet is broken, but a revolutionary technology that could fix it is coming.
by Daniel Morgan
The way data moves on the Internet hasn’t really changed in decades. From its inception until now, the Internet has become increasingly centralized, relying on growing acres of server farms. Each year the farms grow, users lose their ability to manage their own data, and the companies that control that data grow larger and richer. We’ve habituated this network design into our personal lives, laws, and commerce. Web services and business models will continue to build on this prior art unless something changes.
The SAFE Network could chart a completely new course, and it is my hope that we’re going to hear a lot about it in the coming months. Hoping to replace our centralized Internet infrastructure with a more efficient, privacy-aware, decentralized infrastructure, the SAFE Network could be a game changer. As an advocate for a more open Internet and someone who cares about how people use and understand it, this project really excites me. Since so few people have been exposed to the ideas in the SAFE Network, I put this together to answer these questions:
- Why does the Internet need the SAFE network?
- How will individual users benefit from the SAFE network?
- Why should developers and companies who build humanistic technology and services use the SAFE network?
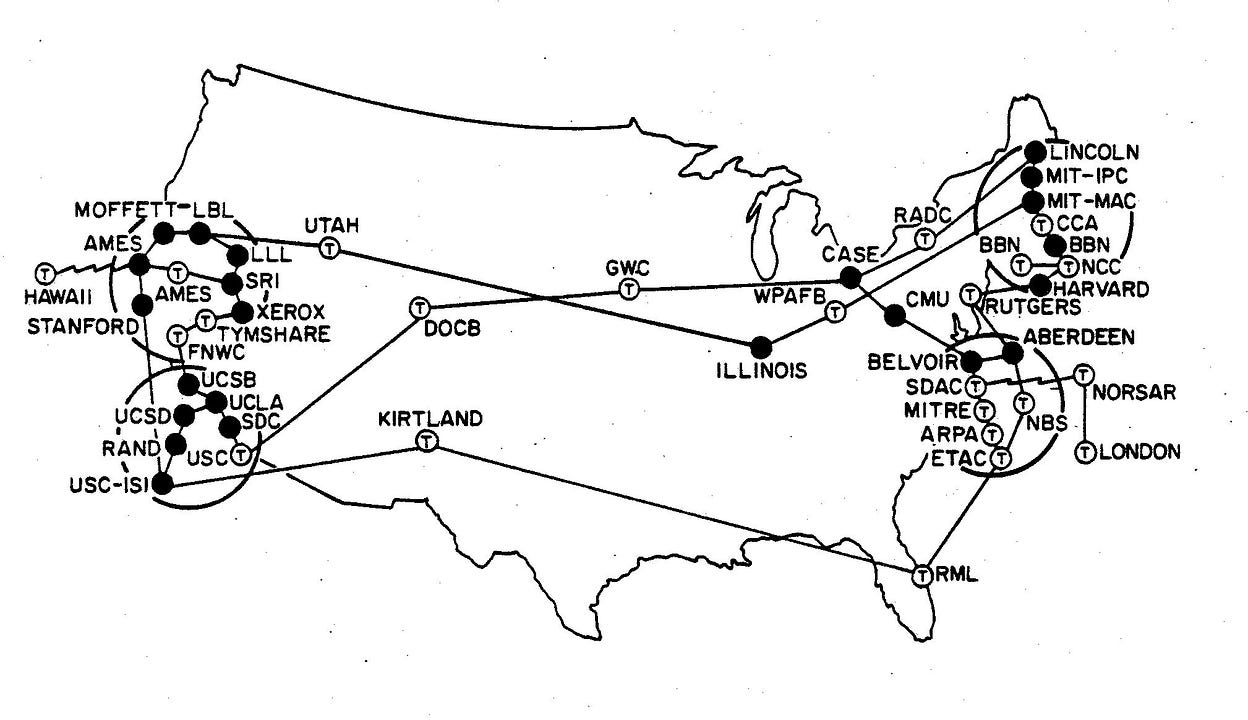
ARPANET, one of the first networks (1974)
How does it work?
The SAFE network distributes the storage and transmission of data through its users, holding privacy and data protection as core principles. This is a huge change from what we have unfortunately come to understand as normal. The SAFE network has been under development since 2003, but in the last two years the momentum of the project has exploded thanks to a successful $6 million funding round and a growing community of supporters. MaidSafe and their non-profit arm, the MaidSafe Foundation, manage development of the open source project. They explain the project as a network,
“…on which application developers can build decentralized applications. The network is made up by individual users who contribute storage, computing power and bandwidth to form a world-wide autonomous system.” Maidsafe.net
The SAFE network will consist of individual nodes run by people like you and me who share resources to build a system that manages itself. As data and network traffic on the network grows, the network architecture morphs to manage its own growing resources. Data is encrypted at rest and in transit, and the entire system optimizes itself autonomously.
Servers are Unnatural
When the World Wide Web came on the scene in the 90s, slow modems connected to larger centralized machines. This made sense at the time because bandwidth and disk space was expensive and scarce. This device → server model has persisted, and today’s world of powerful, resource-intensive data centers continue to send data to thin clients capable of much more. Today, many of us have unlimited data plans, powerful 64 bit mobile devices, and desktop computers with hundreds of gigabytes of free space sitting idle on desks around the world.
The SAFE network drastically changes how we negotiate our own relationship with data, each other, and with private companies by encrypting all data and entrusting it to zero-knowledge peers. It is a collectively-managed, massive Internet-scale disk.
| Left: TCP 1971–today | Right: Decentralized data transmission systems |
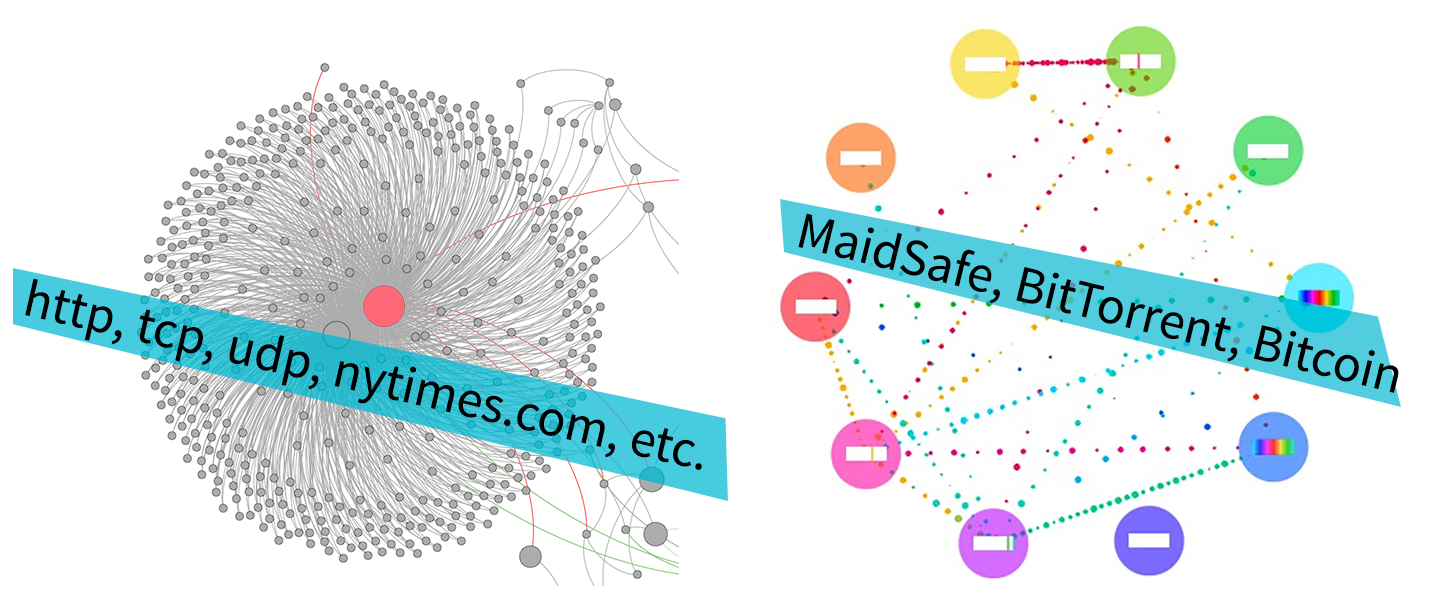
Whose data is the Internet built for?
The SAFE network excites me because data and privacy management should be accessible.
Only the most tech-savvy digital natives fully manage their own communications, storage, and data. Protecting and archiving data, not to mention running home servers for email or storage, is a technical challenge that most people don’t have the time or resources to manage.
Cloud services complicate our relationship with our own data. Thousands of pages of Terms of Service agreements define your relationship with a lifetime of emails, photos, and videos. Those ToS agreements devote more words to offsetting liability for the host than protecting what is yours.
Cloud services have enabled a virtual panopticon, a tragic side effect of networking technology the founding mothers and fathers of the Internet did not intend. Networks have grown and consolidated under the management of publicly-traded companies which excel at harvesting data from their users in exchange for free services. For many of you, this is not news. It shouldn’t be something we take for granted. Jaron Lanier’s book, _Who Owns the Future _covers this trend and potential futures clearly.
We desperately need to repair our relationship with our own data, seek out solutions to regain control, and push services to reduce the amount of digital exhaust collected as a part of their daily business.
MaidSafe (the company) and the SAFE network just might correct this course: once the SAFE network boots up for its first day, Internet users everywhere will be able to choose between the old model — services built on an Internet designed to favor consolidated control over data — or a new experiment that promises to deliver the opposite.
David Irvine, MaidSafe’s inventor and lead engineer, modelled MaidSafe on one of the world’s most organized and perhaps most resilient species — ants. Just as ranks of soldiers, foragers, harvesters, and cleaners form a hive, SAFE network participants form a powerful and collaborative network based on carefully defined roles.
Biomimicry in computer systems is nothing new, but concepts like fault-tolerance, ‘self-healing’ properties and ‘Decentralizing all the things’ could be reframed to ‘Biomimic all the things’ because decentralization is arguably the most optimal state for complex network systems. Translating this basic ideal to computing resources leads to remarkable resiliency and power. David Irvine’s project has been about distributing intelligence and resources, not concentrating it in a single location:
“People talk about AI as building larger smarter computers (IBM Watson, etc.). My conjecture is that it’s not a large thing you build, it should be like ants. Lots of very small things with very few rules that are easily followed.”
David Irvine in his blog post “Why do I keep going on about Ants and Nature”
A few months from now, here’s how you might use the SAFE network: You’d allow the SAFE vault application to store data on a portion of your disk. As your vault and others like it grow, the network organizes itself, (sort of) like the image below, with individual nodes protecting and distributing data based on their ‘closeness’ to other nodes.

So, why would you want to devote your resources to the network? The more resources you devote to the network, the larger your ‘safecoin’ reward. The SAFE network consists of a brilliant technical achievement, and an as-yet untested reward system for encouraging resource utilization and ensuring no one cheats. When the network needs more resources, rewards for providing resources rise. The details are fascinating.
While every computer can respond to data requests, some respond faster due to their geographic location and/or disk speed. Incomplete, corrupted, or garbled responses earn you nothing and lower your trust ranking. The network assigns roles based on this ranking:
This diagram outlines the relationship and separation of duties between the encrypter of private data (MaidNode), managers of private data accounts (MaidManagers), managers of the managers of availability of data (DataManagers), managers of the availability of data (PmidManagers), and the actual low level process which stores the data (PmidNode) (Roles on the MaidSafe network)
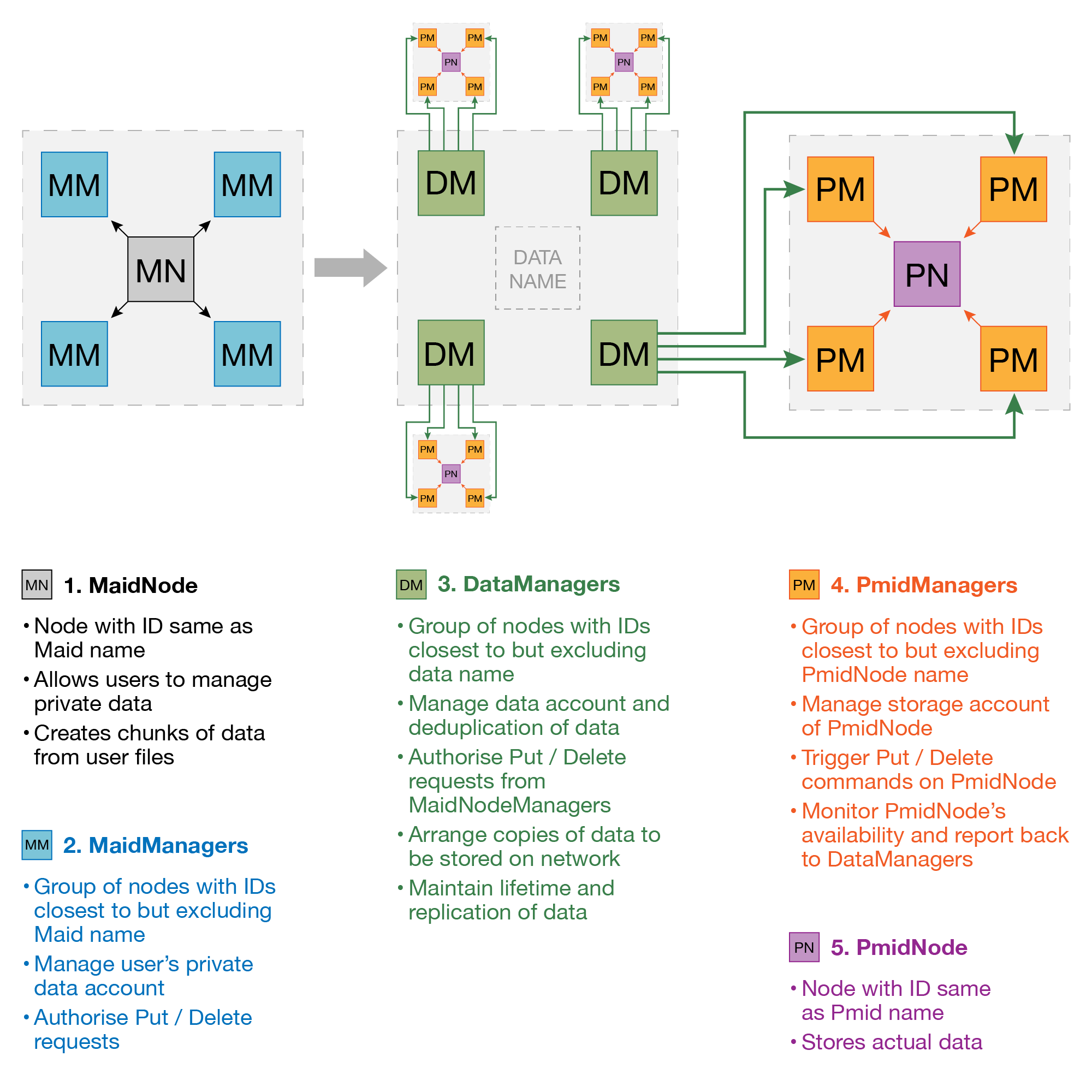
So many aspects of the SAFE network deserve much more detail and attention than I’m giving it here, and I urge you to dig deeper into its structure if you’re curious. Check out the Wiki, follow the detailed developer updates, or subscribe to Project Safe News.
Correcting a Faith Deficit

The __Archive Team warrior_ scrapes & saves data._
Every day we hear about stolen passwords, lost identities, misplaced data, and services shutting down and deleting user data. The site ‘Closed Club’ chronicles this data impermanence while the Archive Team tries to save what it can. For companies with no data portability or export plan, the Archive team will rush in like a swarm of firefighters to the burning digital libraries around the web. We’re starting to understand that you should never trust a corporation to do a library’s job, but making remembrance part of the digital experience is not something we have come to expect. With the SAFE network, data = sacred.
On the services side, managing and securing user data is incredibly complex. It takes huge security teams and proactive bug bounty programs to keep systems secure. Normal folks don’t use two-factor authentication. Cottage industries have emerged to alert users when their personal information appears on the darknet.
On the legal side, legislation threatens to upset the already unnatural balance between service providers and users, making providers liable for every word posted to their services. We allow two people to communicate in private walking down the street, but governments seek out ‘backdoors’ and ‘golden keys’ to listen in on private communications online. Governments without any understanding of the technologies their citizens use continue to ban encryption or hack their citizens. This is a hugely important problem that is more cultural than technical, and it taints our collective view of what Internet can and should be.
“The amount of control you have over somebody if you can monitor internet activity is amazing.”
Sir Tim Berners Lee
How should companies behave?
No law declares how a company should handle their data when closing down or selling off. Few companies take the right approach here, as Natasha Singer recently covered in this NYTimes feature. Similarly, few companies build out complete data export systems.
The blogging service Posthaven addresses this problem as their singular purpose. Posthaven promises to (1) survive as long as they have customers and (2) build out features that do not impact #1:
First off, we’ll charge money. There’s no question the site will run when you know how to pay for the servers. Then we’ll keep improving the site the way a good caretaker would tend a garden. We’ll make sure things are clean and safe, and replace things when they get worn, or when it’s ready for a renovation. Think of us as long term data custodians.
via_ Posthaven_
The SAFE network would be a data custodian that developers can plug their applications into. If the application disappears, the data will remain. “Will this service exist in five years?” is a question worth asking before signing up to any service, but the SAFE network changes this expectation. This aspect of our relationship with the Internet and Internet services needs repairing. The SAFE network is no magic bullet, but it introduces a possible future where what we create is protected collectively by those who create it. Data will not need an ‘export plan’ when it remains cryptographically linked and controlled by its creator.
Developers weighing the pros and cons of cloud hosting services, managed hosting environments, and various server stacks will soon be able to plug into the SAFE network as their backend storage. Instead of defaulting to Amazon’s cloud or their own racks to manage storage and encryption, MaidSafe offers a private/redundant/always-available data store.
When the service launches, I’m hoping that the technology community takes a close look at its benefits for the storage and transmission of all types of data. Here’s a quick overview of the SAFE network goal:
- Redundant self-managed storage
- Encryption by default
- Fast and intelligent routing
- Intelligent caching — popular data spreads itself to more nodes
- Incentivized transmission and retrieval. The incentive scheme rewards bandwidth and disk space similar to how Bitcoin miners are rewarded for computation. Farmers (like Bitcoin’s miners) are MaidSafe’s data managers. App developers are also rewarded when content associated with their application becomes accessed.
- Self-authentication & Zero-Knowledge. The system is designed from the ground up for data minimization. Designed to allow user signup for applications without a sign in server.
- The MaidSafe team runs the open source ship, and holds defensive patents. The system resists human control once running.
If all goes well, in ten years these features will be boring in the same way that BitTorrent has become boring — it just works, and we can depend on it. The SAFE network could pave the way for a slew of new services where privacy and data protection are taken for granted and digital services behave more like public services.
SAFE stands for Secure Access For Everyone. It’s not a crutch or stopgap for the issues our current Internet fails to resolve, but a huge shakeup. We shouldn’t give up in the face of these problems, we just need to start fresh. I’m happy to see it approach day zero.
Link to original article on Medium.com
*This article originally published by Daniel Morgan on Medium.com, and is used with his permission. Thank you, Daniel.
